This post only applies to the original Apple TV, not the “4K 1st Generation”. The original Apple TV has a light gray outer case, as opposed to the black/dark gray of later generations. Installing Linux The 32-bit Intel processor will limit options for distributions since most modern releases are 64-bit only. If you need the…
Modifying an Inkjet Printer for DTF Printing
Getting Started What is DTF? Direct to Film printing (DTF) is a method of transferring digital designs to shirts or other garments. DTF ink is printed onto a carrier sheet, usually PET (Polyethylene Terephthalate), and the carrier sheet is heat-pressed onto a garment. What type of inkjet printer is needed? Ideally, the printer will need…
Designing a 7-node Proxmox/Ceph cluster in Blender
I’ve been wanting to build a Proxmox cluster for a while — mainly to get a feel for Ceph storage. I’m firmly in the ZFS camp, but I do see the appeal of distributed storage paired with a high availability cluster. I plan on using this for my web development stack — LAMP, MEAN, etc…
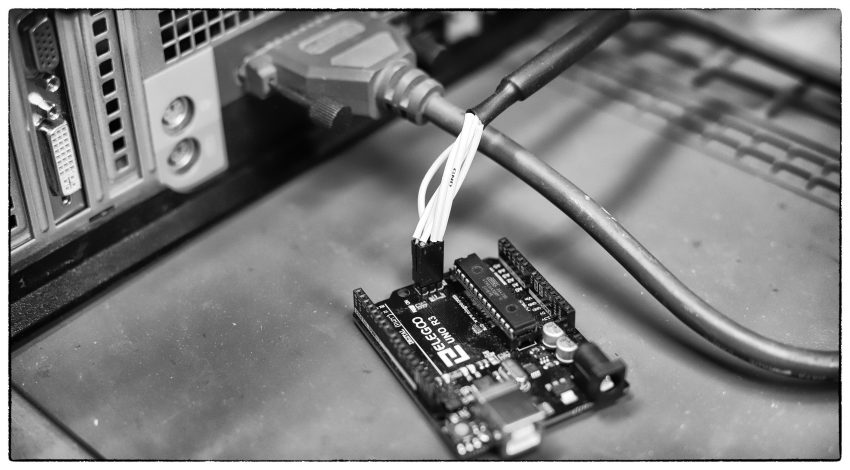
Burn an Arduino Bootloader via Parallel Port
It is possible to burn an Arduino bootloader with nothing more than a computer and parallel port cable. Finding a system with a parallel port is the hard part. Anything newer than a Core 2 Duo will be hit or miss for legacy ports — so a pre-2010 computer is a good place to start….
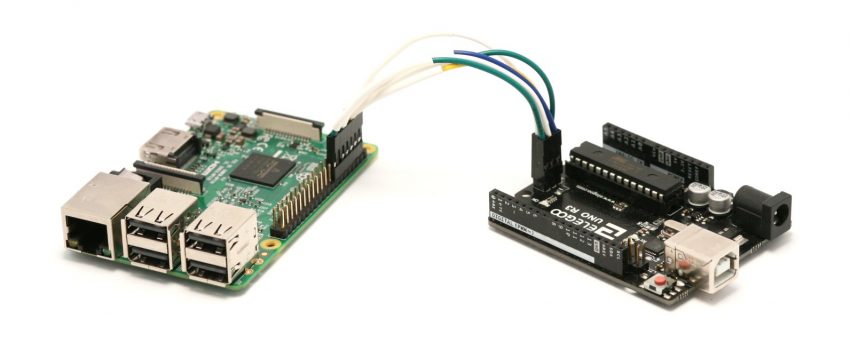
Burn an Arduino Bootloader with a Raspberry Pi. The easy way.
This process uses a modified version of the official Raspberry Pi OS (2020-02-13-raspbian-buster-lite.img). It has been configured with the tools necessary to burn an Arduino style bootloader using the Raspberry Pi’s GPIO pins (described here). Brief summary of steps: Wire Raspberry Pi GPIO pins to Arduino ICSP pins Boot the custom Raspberry Pi image Connect a…
Programmatically Validate Addresses with the UPS Developer Kit, Tracking Integration
If you have an e-commerce website, you can validate shipping addresses on the front end to reduce delays and minimize costly returns due to bad addresses. Going further, you can also script and automate address validation for batch imports into UPS Worldship. This process will only apply to addresses in the United States, since UPS…
Managing Hyper-V Server in a Workgroup Environment
Hyper-V Server is great and it’s also completely free. Yes, Windows 10 Pro comes with the option to install and run Hyper-V, but anyone running more than a couple of virtual machines will eventually gravitate towards a dedicated virtualization server. So how do you manage Hyper-V Server if it doesn’t have a GUI? Any Windows…
Securing Remote Desktop with SSH Tunneling
The dangers of exposing Remote Desktop Protocol (RDP) to the internet are well documented. It’s no surprise that a tool designed for ease of use has become a prime target for scripted brute force attacks and other exploits, allowing compromised machines to serve as attack vectors for Ransomware. There are several practices for enhancing Remote…
Control Two Independent Stepper Motors with an Arduino
I work with stepper motors a lot. My projects typically include multiple motors running off of a single microcontroller. Everything is great when you’re running all of them at the same speed. But what if you need each motor to run at a different speed? at a different time? or you need to do something…
Public Key Authentication with PuTTY
Public Key authentication is one of the safest ways to log into a server. Instead of using a plain text password, Public Key authentication uses a Public/Private key pair to identify authorized users. The target server stores the Public Key while the user holds the Private Key. Step 1: Generating Public / Private Keys with…